Secorun Access Control is an advanced physical access control and monitoring system for people and vehicles entering the facility and its certain sectors, departments and areas. It allows managing the people, vehicles and items (PVI) traffic and monitoring their movement at the facility in terms of time and position. It is a tool offering a full spectrum of single and multi-component methods and technologies of identification and authentication such as: RFID, NFC, Bluetooth, QR, biometry, PIN/password, LPR. The choice of the method and the technology is made by the analyst based on the Client’s requirements in terms of the security level of the process, the area covered and the comfort of using the solution. Access Control is a wide spectrum of functionalities, providing multi-level management of users’ entitlements to the system functionalities and their access to certain user and user groups data ranges. Among other functionalities, the product provides the ability to automatically adapt the entitlement level through time, to use “lowest required entitlement level” policies or to parametrize the entitlements according to the CRUD rule.
“The Access Control is not only a system of constructional and organizational elements and the devices necessary for controlling the access in the company. Above all it’s a growth of the security level of people and classified company data.
Our clients’ satisfaction comes from the completeness and quality of our solutions. That’s why we focus on the newest technologies and a good, experienced team of analysts and developers.”
Jakub Bortkiewicz
IT Product Manager
Bussiness benefits of the Access Control
Automatic reporting of the subjects’, contractors’ and visitors’ presence in the areas – thanks to that functionality it is possible to verify the real time of a presence compared to initially contracted hour count.
Simplification of the management process. Unlimited scalability of the system allows building a centrally controled, distributed access control system, supervised by an operator with access to selected locations.
Ability to share the data collected by the Access Control system with any of the integratable platforms. Employee data, permissions, medical examination and alert situations can be exchanged in any direction.
Supporting any control process at the organization, that would allow the analysis of e.g. work or process efficiency using the data reports registered in Access Control processes.
Digitalization of data and documents flow. The informatization of the people and vehicles traffic handling process eliminates the necessity of maintaining the paper form of various documents, registries and certifications of accessibility to the restricted area.
GDPR compatibility. The system allows recording the personal data according to the GDPR regulations and provides the security of the collected information in terms of personal data processing.
The ability to integrate and use the Access Control System data in any business process e.g. logistics, production, meal access control, managing the vehicle fleet and much more.
Access to advanced reporting. Every manipulation of access data is logged and available in the permission modification report, increasing the control and security level in the company.
USE CASE 1
In a big company, with extensive infrastructure of a few hundred access control points and a complex organization structure, one of the Security Department employees gets information about a new worker being employed. Her_his role is to prepare an access card and set the permissions to allow traveling around the facility. Setting the areas and access points for the new employee is a time-consuming process, it requires collecting and verifying information from many different departments.
How can this process be optimized, automated and digitized? Could the stakeholders of the decision process grant permissions with just one click? Could the system fully take over the control over the permission granting process, using information about the employee’s position and function?
USE CASE 2
While performing his duties, the electrician fell off the ladder after being electrocuted and got injured. Mr. Jacob, the OHS manager, got informed about a dangerous incident at the facility. During the initial investigation, it turned out that the electrician’s SEP qualifications ran out of date a few days before the incident. The OHS manager and the investigating committee are trying to work out why the worker was allowed to perform duties.
Could this situation be avoided? If there was a system at the company, automatically controlling the access based on the validity of visitors’ tests and training, would such an incident occur? Could the system deny the access to a worker without valid qualifications?
Highly customizable advanced solution
The Secorun Access Control is a scalable platform, providing the ability to effectively manage local or multi-branch company infrastructure. This elastic tool allows itself to be integrated with any open-source informatic platform. The client can forget about keeping double data records. During the implementation stage, the competencies of the used systems are being set. The data registered in the overriding systems are automatically exported to the access control system. Personal and employee data, information about cards, permissions, events, alert situations can be exchanged and shared in any direction according to the business process requirements. Information from the dependent systems, such as the employee training system or RCP system, can automatically determine workers’ and contractors’ permissions to move around the company.
Extensive possibilities of the system’s configuration provide a wide package of settings and adjustments to meet the expectations of the most demanding clients. The Secorun Access Control is a solution based on self-owned product lines of devices, allowing the specific business logic to be implemented directly into the devices, according to the edge computing ideas. The devices and the software developed by one producer guarantee full compatibility, solution’s stability, wide modification possibilities and, most important, effective service care. The solution provides tools supporting PDI, security officers or data administrators in meeting the GDPR requirements. It opens up a possibility of automatic system data retention in retention groups defined by time parameters. It also allows keeping a registry of applications and other procedures resulting from the applicable law in that area.
“The awareness of responsibility for the security quality of our clients and company data is the key to the implementation of access control system solutions meeting highest technical standards.
Introduction of the access control by using specialized devices, software and authentication credentials not only will improve the access management at the company, but also raise its rank.”
Diana Karcz
Designer
Key functionalities of the Access Control
The ability of integration with any open informatic platform – the system collaborates with BMS and alert systems. It autonomously monitors the device infrastructure functioning and alerts about possible anomalies.
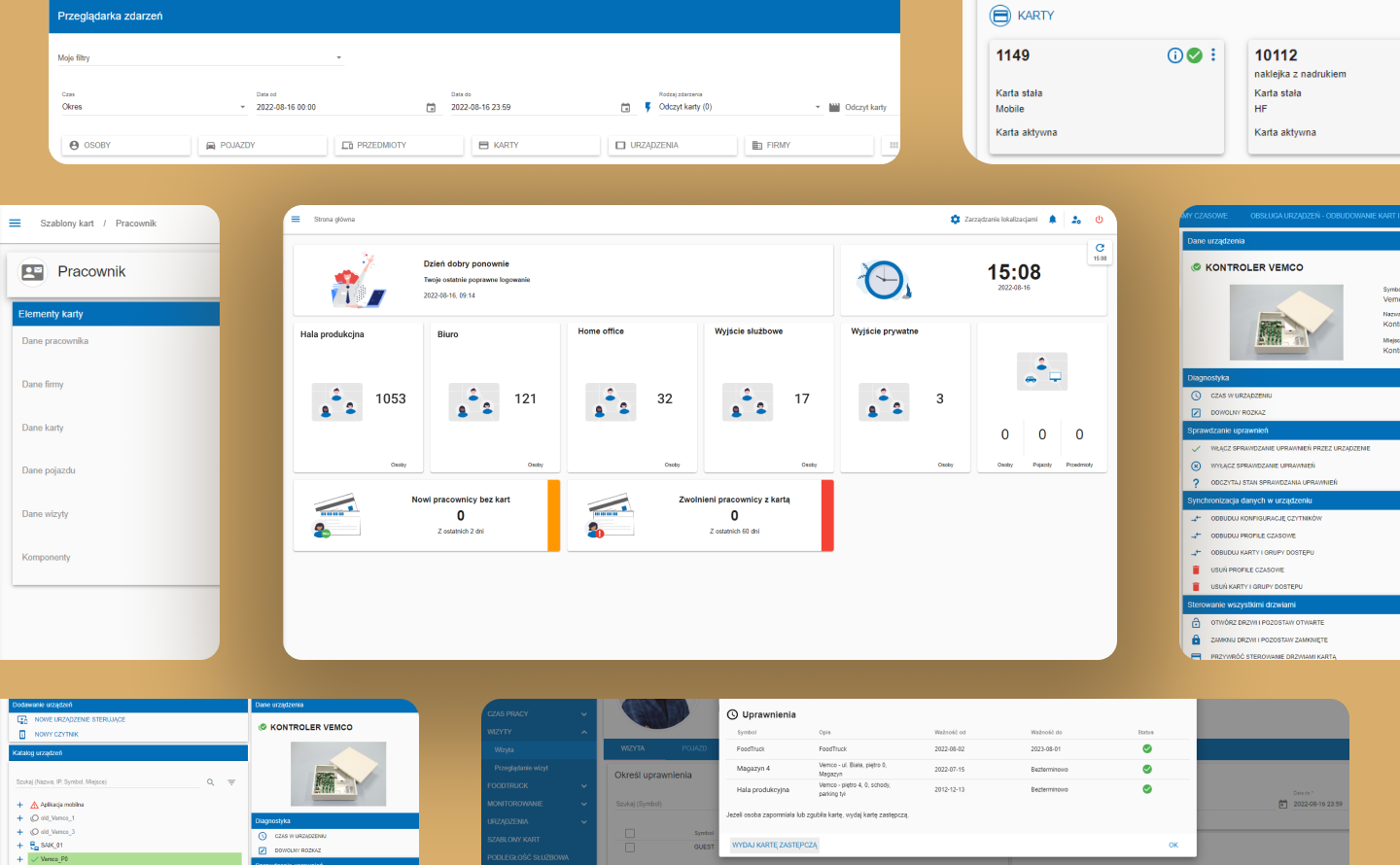
Individually configured DashBoard. It is possible to define shortcuts to the most used application modules – the widget showing the number of guests or the list of people and vehicles at the facility and its areas.
Tailor-made intuitive interface contains all the information necessary for the operator to make a quick decision. The responsiveness provides the ability to adjust the interface components to individual needs of the operator.
Permission management of guests, employees and vehicles module designed to gain all the data required for the operator to make a decision on one screen – for example to issue a replacement card or to block permissions.
Automatic notification of the operators about the occurrence of one of the predefined wanted or unwanted situations such as lack of communication with the device or alert situation happening (e.g. broken door of the server room).
The vehicle traffic control using stationary or mobile terminals that allow full process handling, permission validation and remote barrier control by reading the authorized guard’s card.
Automation of people and vehicle data collection at the facility by using smart identity documents readers.
Predefined reports as a part of individual subscribtions created by application operators. Daily, weekly or monthly compilation of the employees’ or contractors’ time of presence at the company.
Personal data security and consistency – on every stage of personal data recording, the system takes care of its consistency. The system automatically recognizes the possibility of doubling the personal data.
Multi-branch, distributed organizations – within one system instance it’s possible to connect the access control devices with different locations and separating the data from certain locations.

Integration with third-party systems
Secorun Access Control provides the ability to integrate with any open informatic platform. It cooperates with BMSes and alarm systems. It informs visually or sonically about alert events and makes it possible to visualize the events from these systems within its own application. It autonomously monitors the devices infrastructure functioning and alerts the administrator about any anomalies. It comes with self-repair mechanism that starts up automatically in case of a malfunction not caused by a device damage.
Currently, the Access Control is fully integrated with other Secorun Package products:


